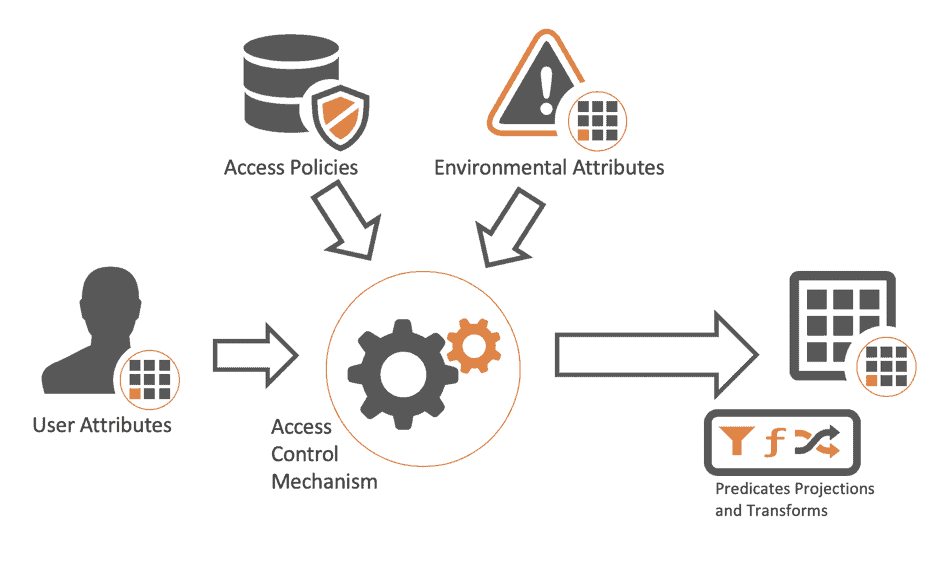
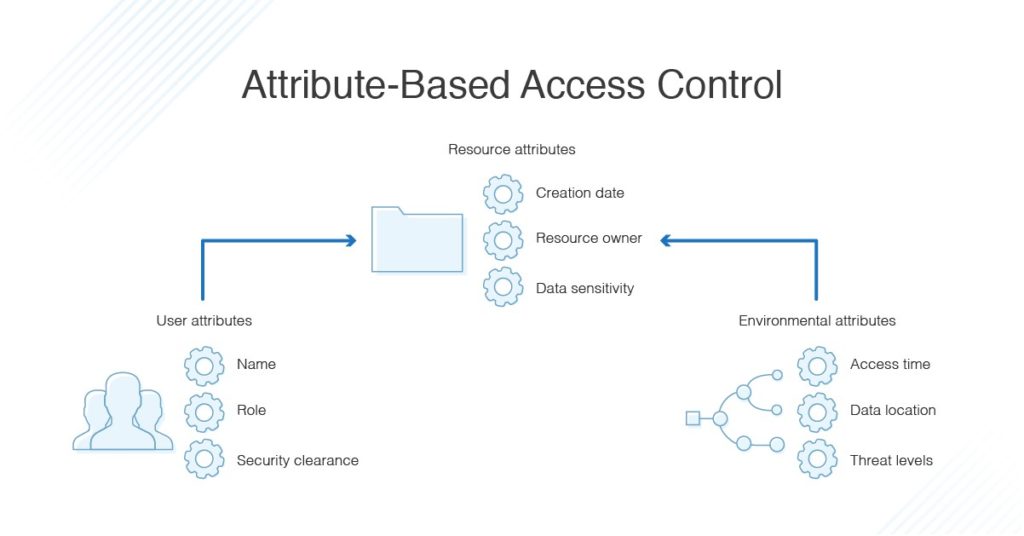
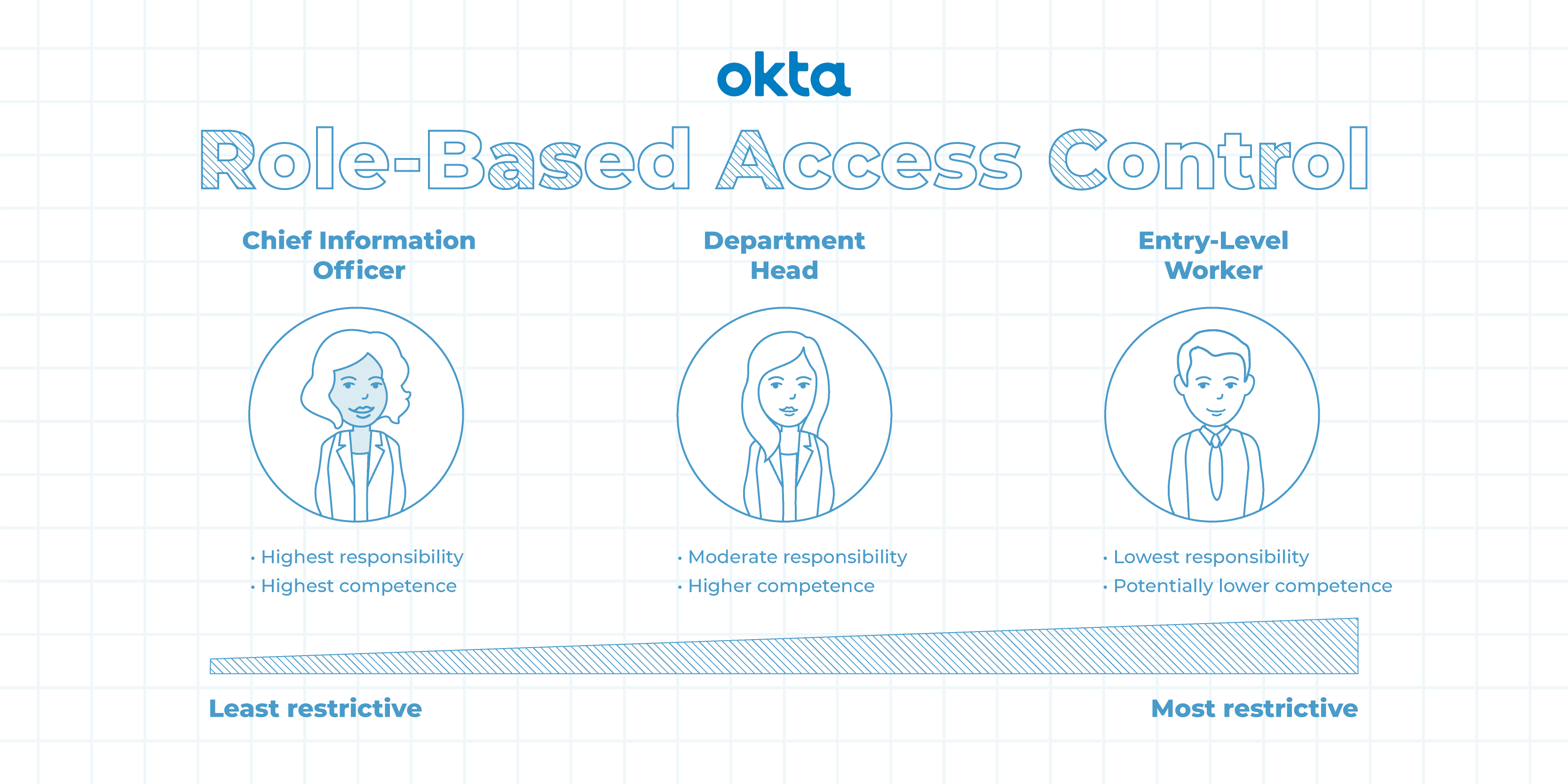
Figure 2 from Comparison of Attribute Based Access Control (ABAC) Model and Rule Based Access (RBAC) to Digital Evidence Storage (DES) | Semantic Scholar
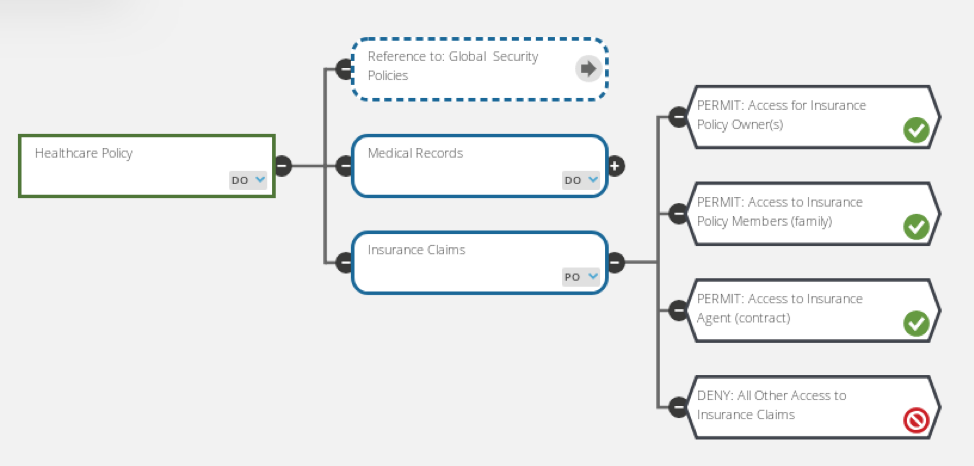
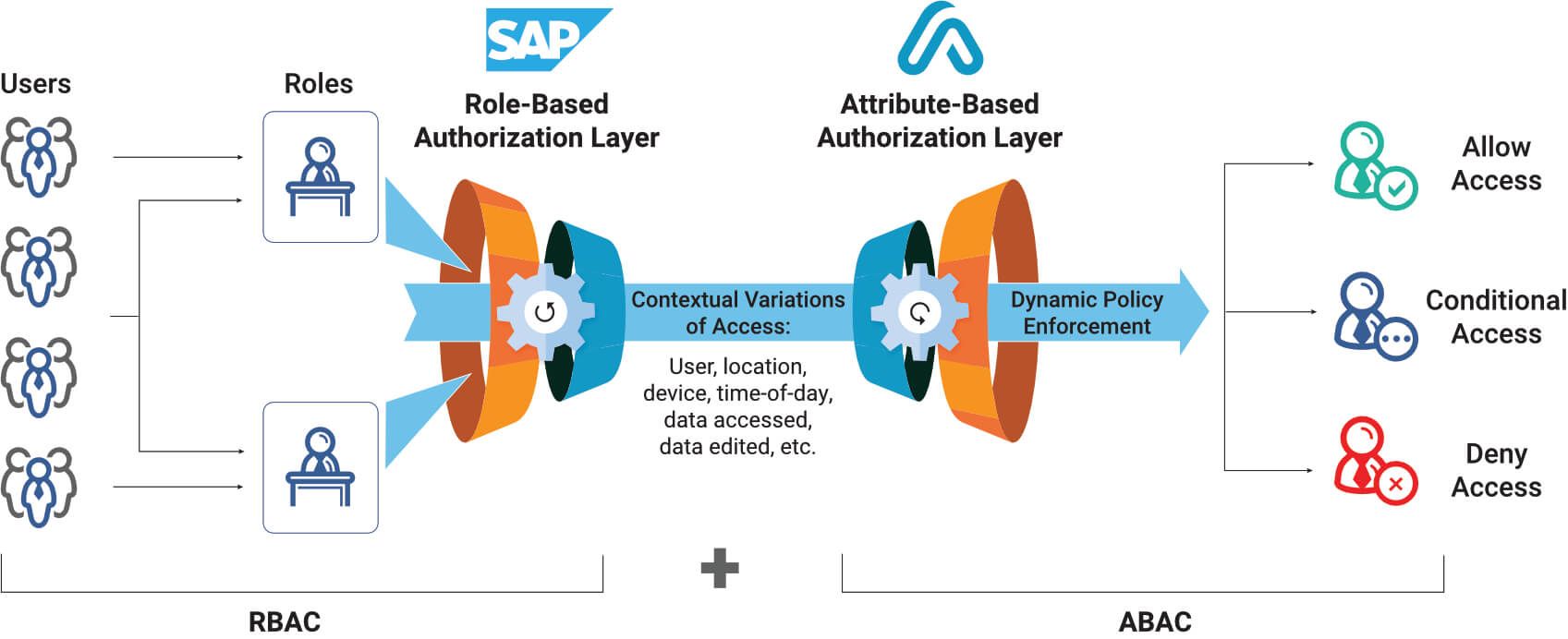
DZone: Why Attribute-Based Access Control - The Evolution from RBAC to ABAC in Data Access Control - Axiomatics
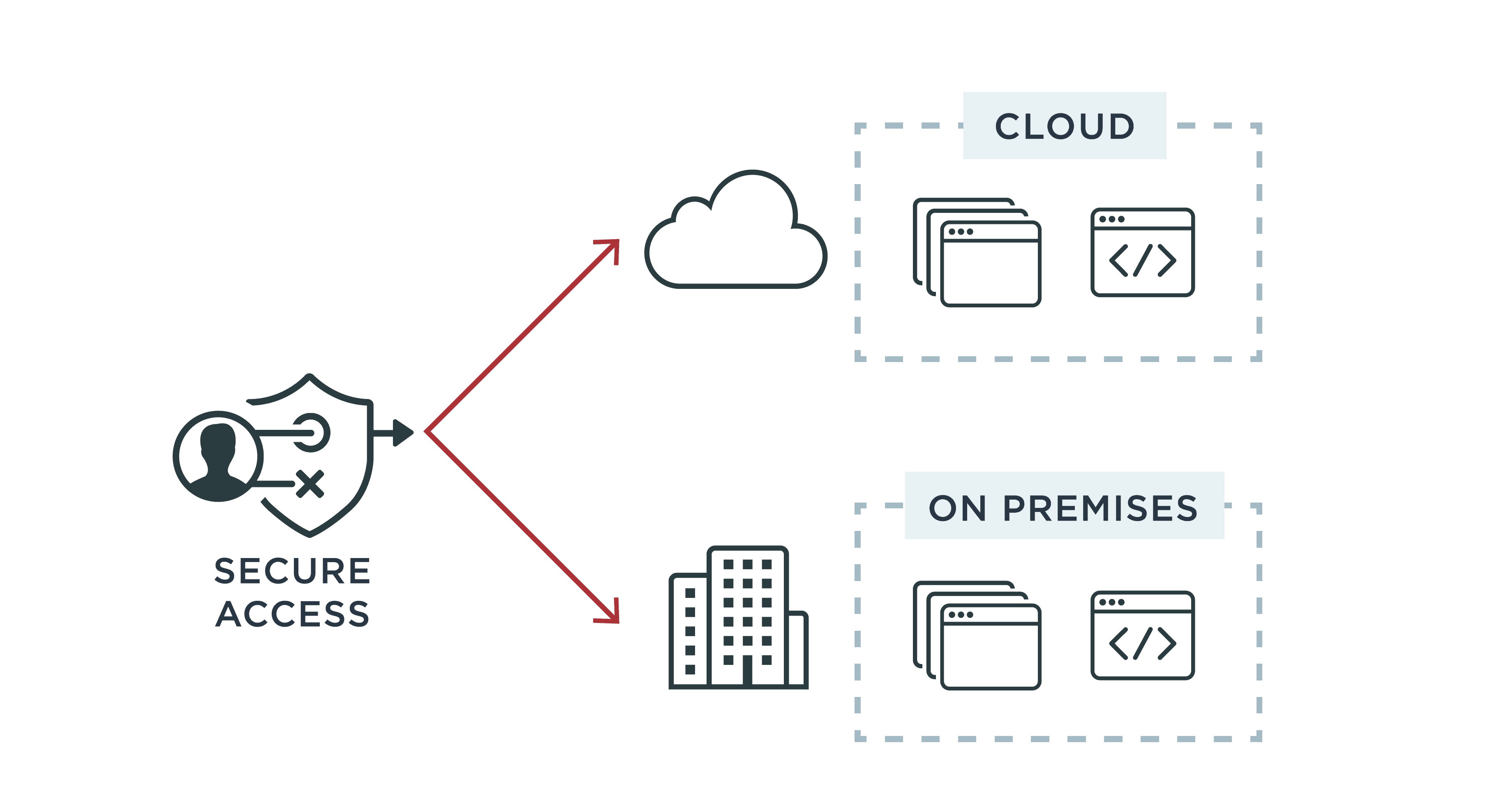









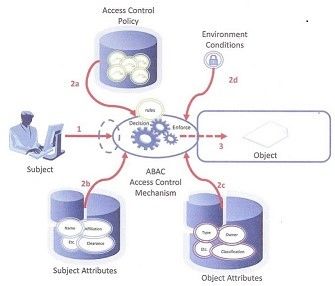
![PDF] Attribute-Based Access Control | Semantic Scholar PDF] Attribute-Based Access Control | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f2d698c5a1819b0cff0c8899b8a391c5721aa2b6/2-Figure1-1.png)