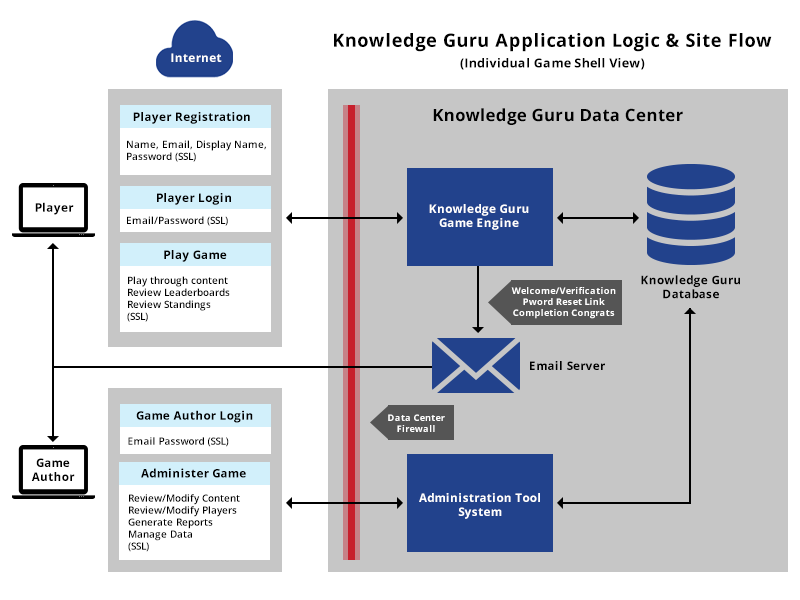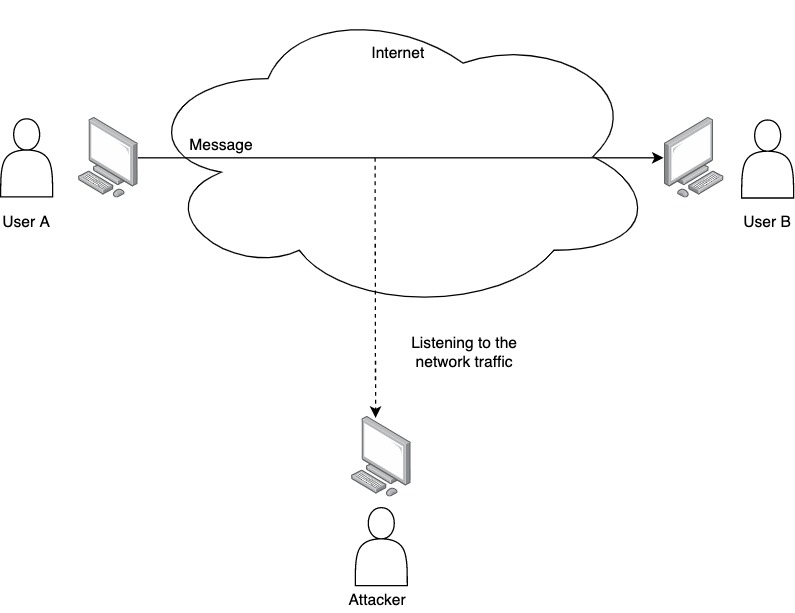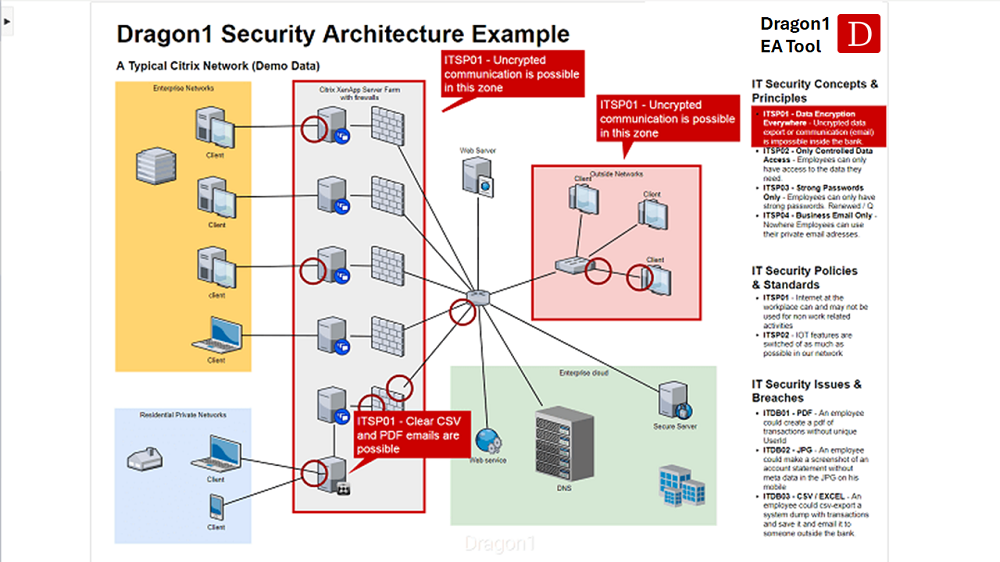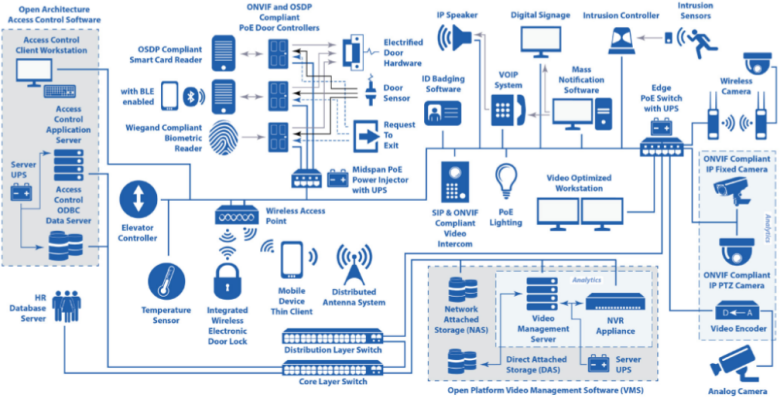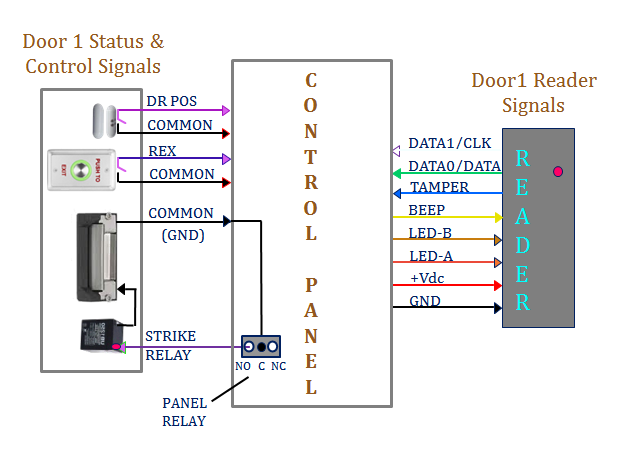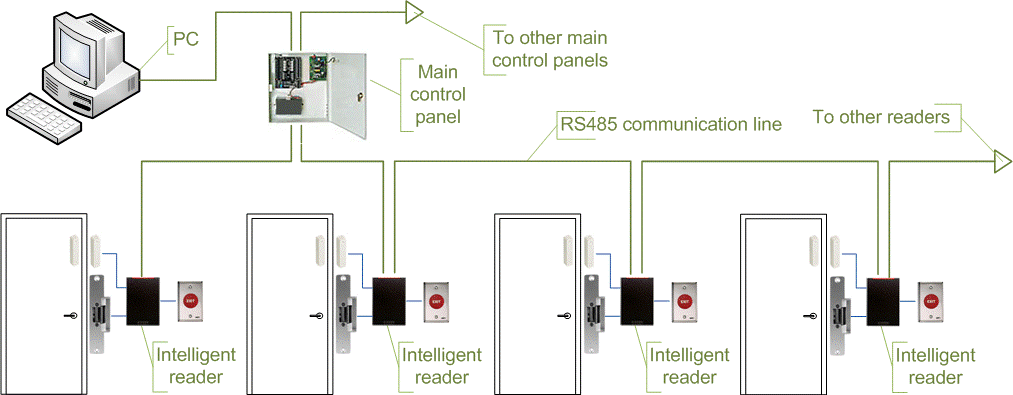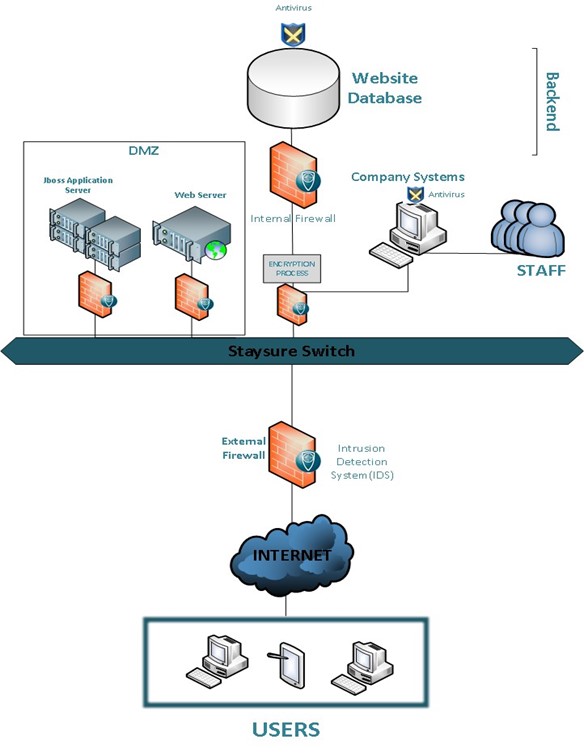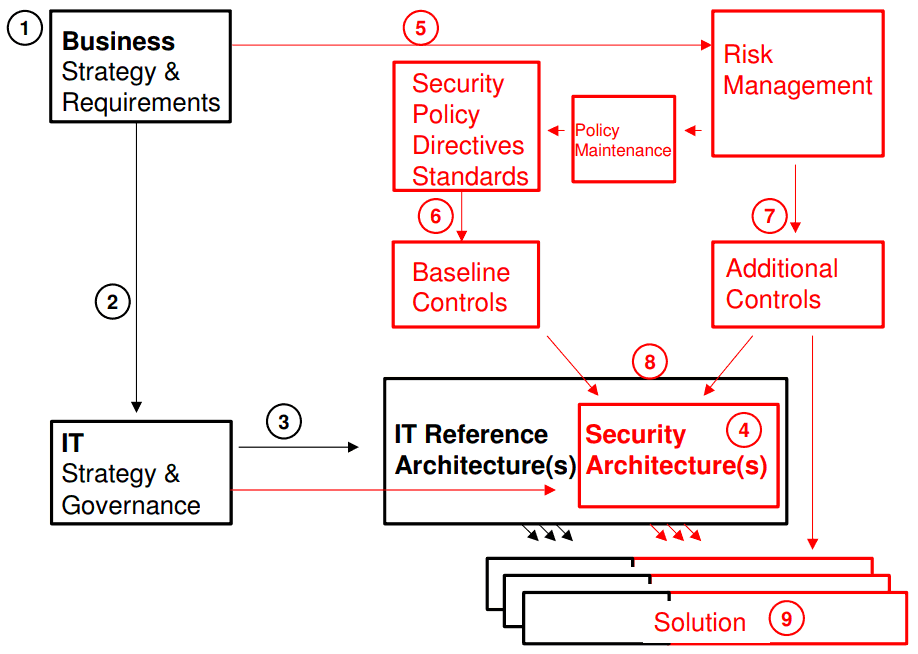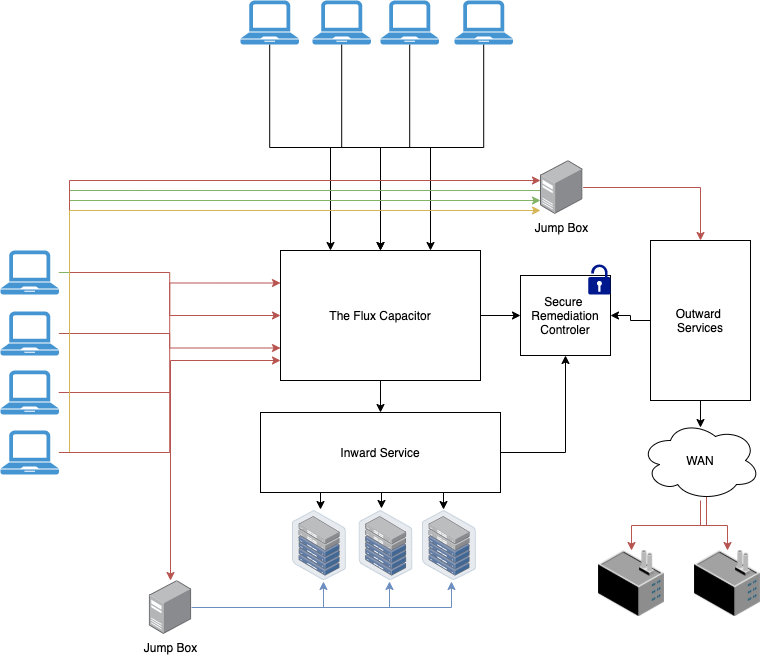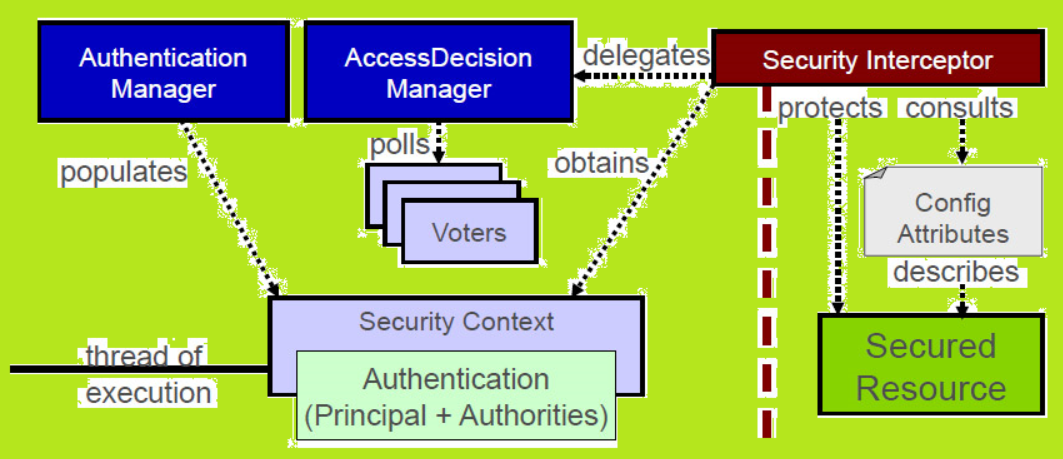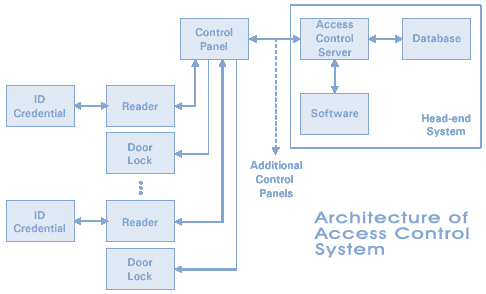
Architecture of Access Control System Access Control time attendance Systems Physical Access Control Systems biometrics safes Access Control Security Systems, Door Access Control Systems, Access Control And Security Systems korea UAE Singapore

Smart Home Access Control architecture & cross-domain communication.... | Download Scientific Diagram

Development of an access control model, system architecture and approaches for resource sharing in virtual enterprise - ScienceDirect