How to design access control system for Saas application | by Anna Savytska | Muzli - Design Inspiration

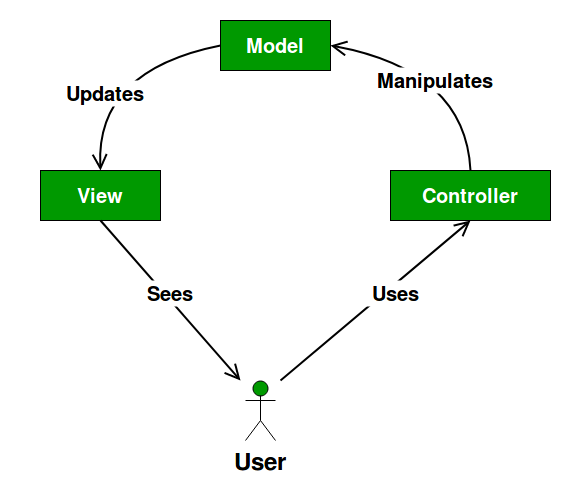
10 Common Software Architectural Patterns in a nutshell | by Vijini Mallawaarachchi | Towards Data Science
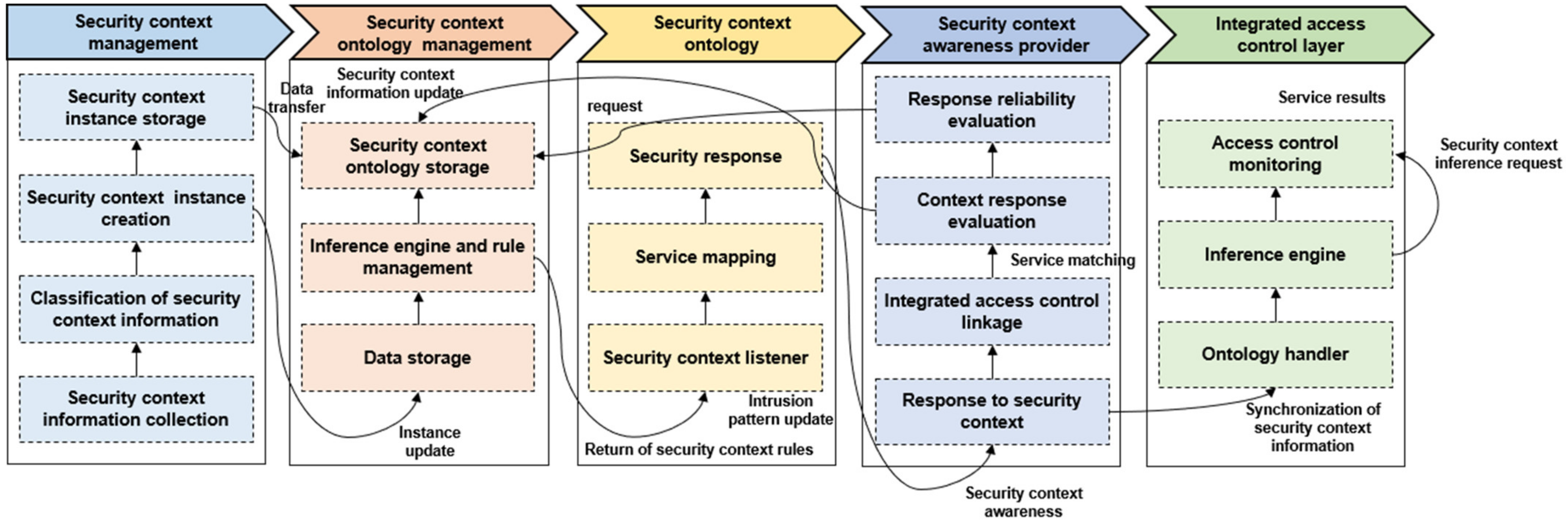
Sustainability | Free Full-Text | Intelligent Access Control Design for Security Context Awareness in Smart Grid

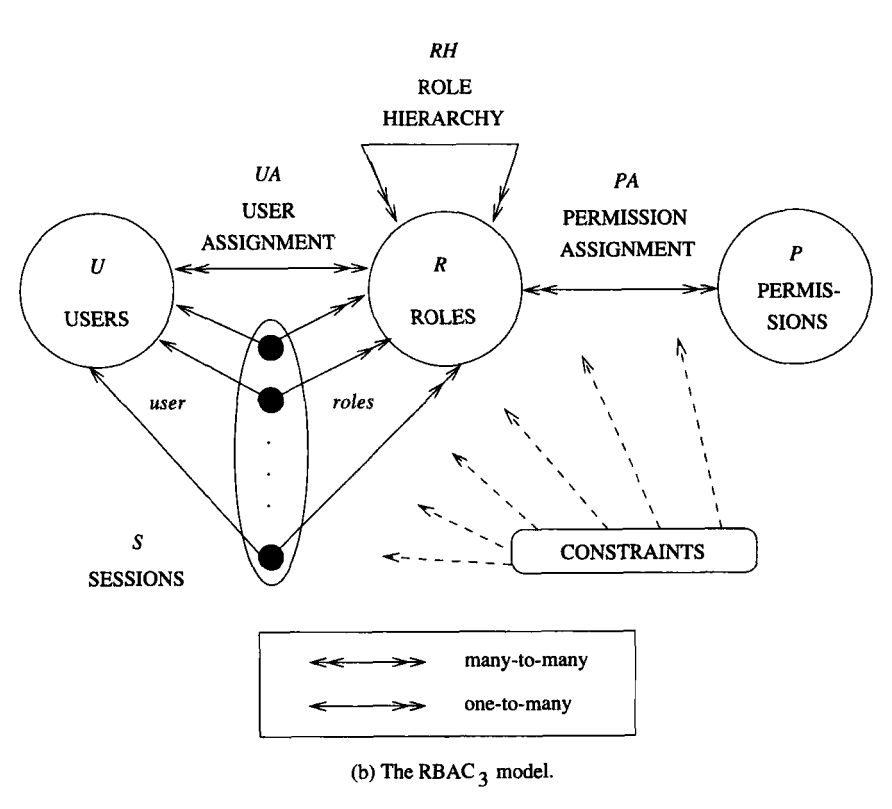
PDF) THE ADMINISTRATOR OBJECT PATTERN FOR ROLE-BASED ACCESS CONTROL | Saluka R. Kodituwakku - Academia.edu
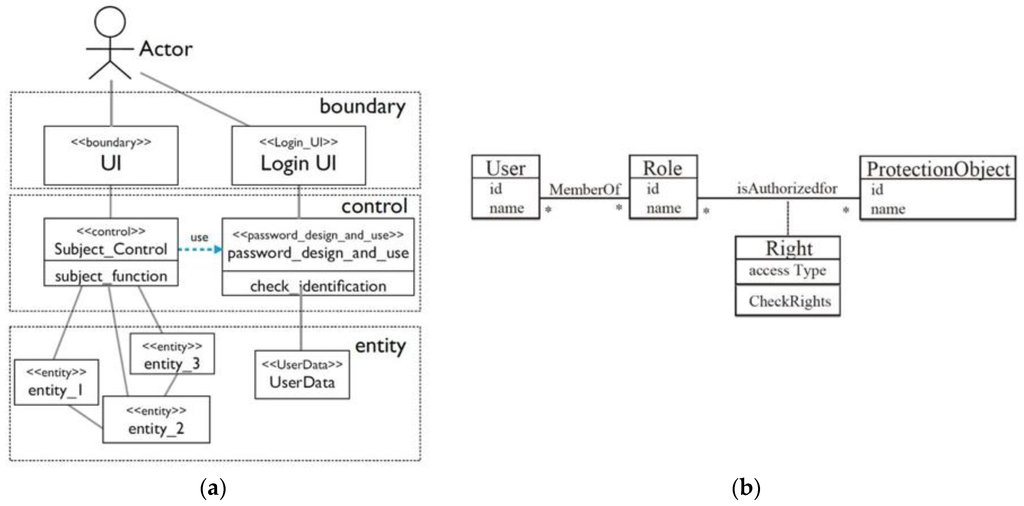
Information | Free Full-Text | Implementation Support of Security Design Patterns Using Test Templates | HTML
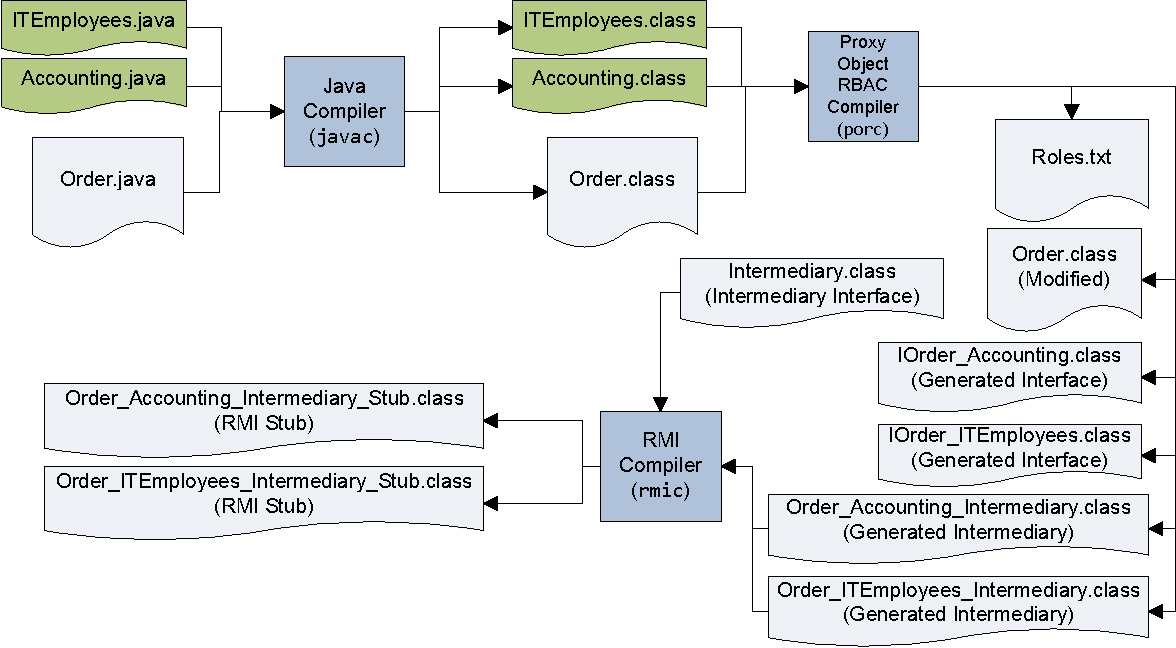

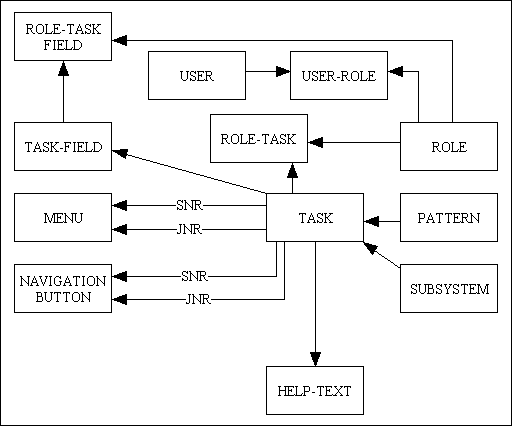
![PDF] Describing access control models as design patterns using roles | Semantic Scholar PDF] Describing access control models as design patterns using roles | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/428010d888b5a8854172e81047c9afb5193b4f6f/2-Figure1-1.png)
![PDF] Describing access control models as design patterns using roles | Semantic Scholar PDF] Describing access control models as design patterns using roles | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/428010d888b5a8854172e81047c9afb5193b4f6f/3-Figure4-1.png)


![PDF] Describing access control models as design patterns using roles | Semantic Scholar PDF] Describing access control models as design patterns using roles | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/428010d888b5a8854172e81047c9afb5193b4f6f/2-Figure2-1.png)