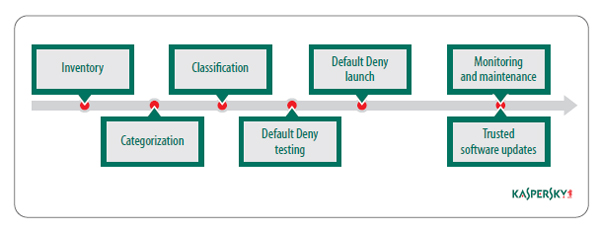
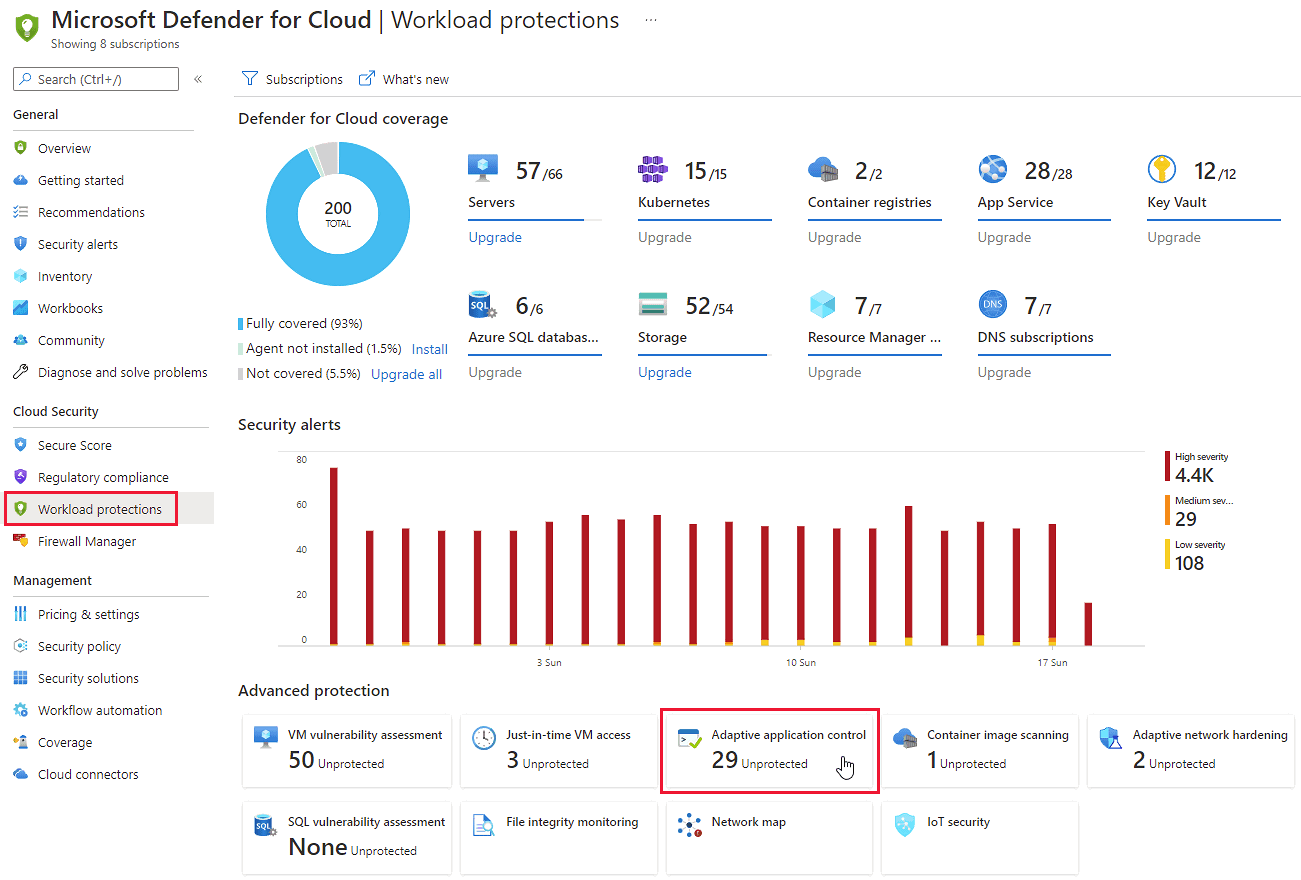
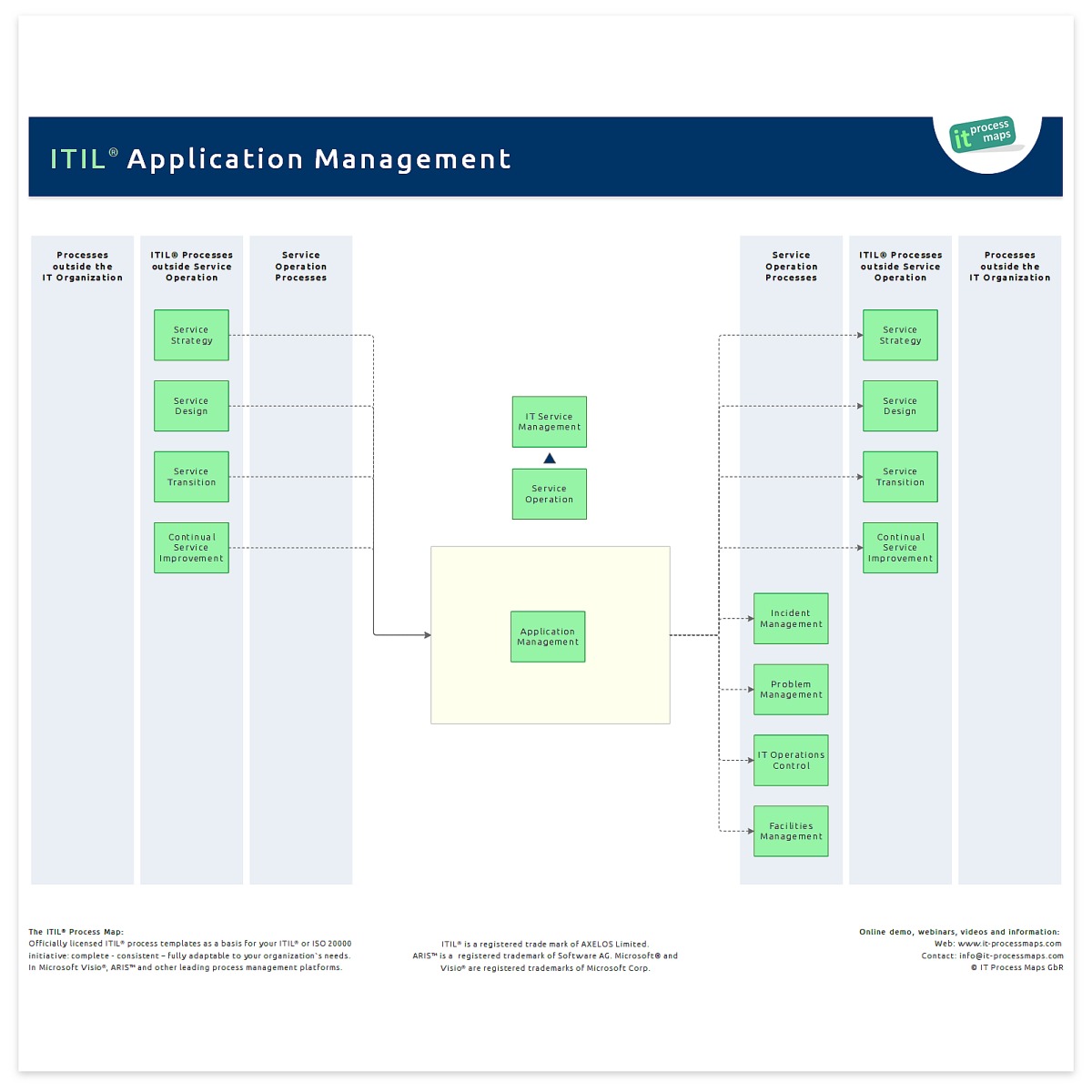
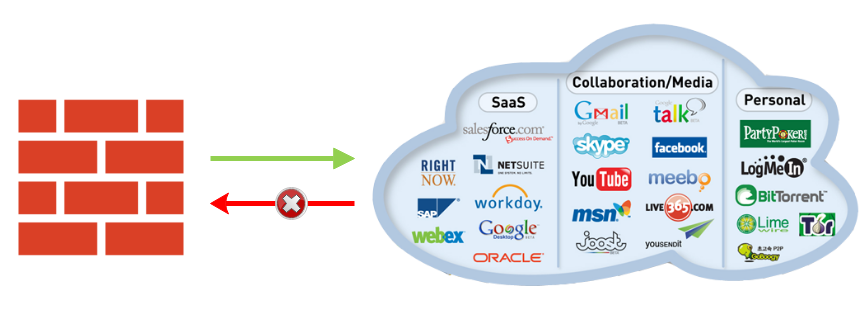
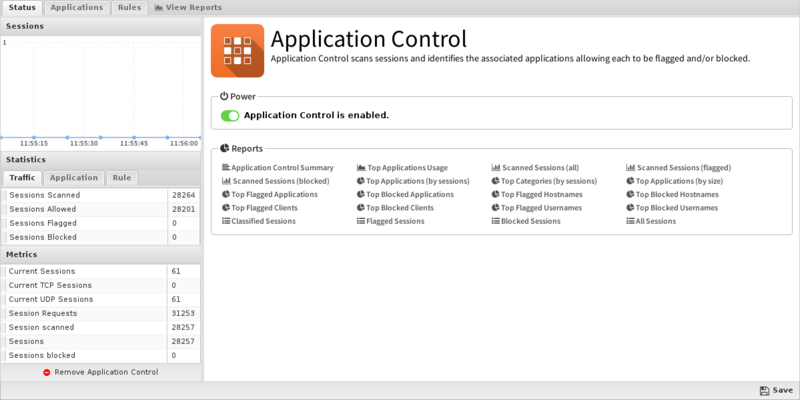
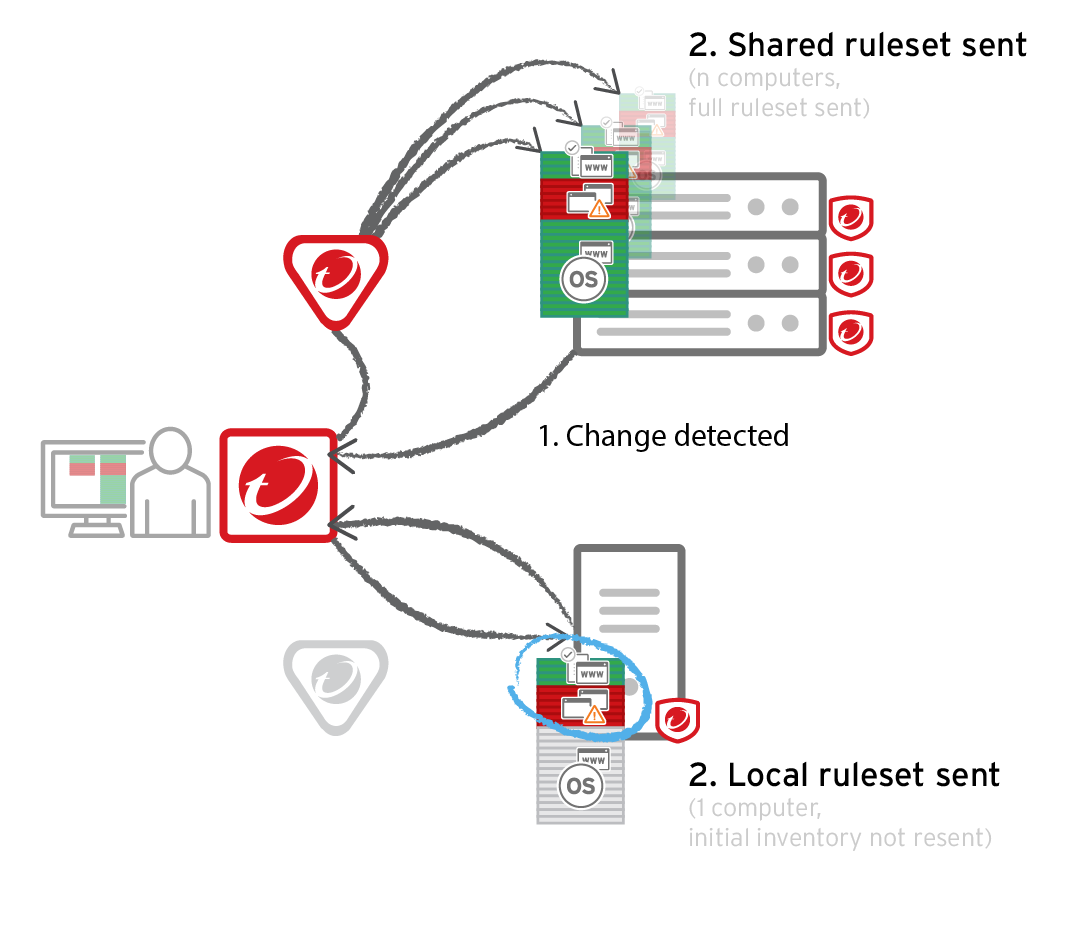
Software di controllo delle applicazioni | Soluzione di controllo delle applicazioni - ManageEngine Application Control Plus

Implementing Application Control and Eliminating Productivity Dips - United States Cybersecurity Magazine

The Five Key Benefits of Application Control and How to Achieve Them – Cyber Security Experts – Middle East | Eastern Province | Al-Khobar, Kingdom of Saudi Arabia