Research Summary: Efficient Attribute-Based Smart Contract Access Control Enhanced by Reputation Assessment - Auditing and Security - Smart Contract Research Forum

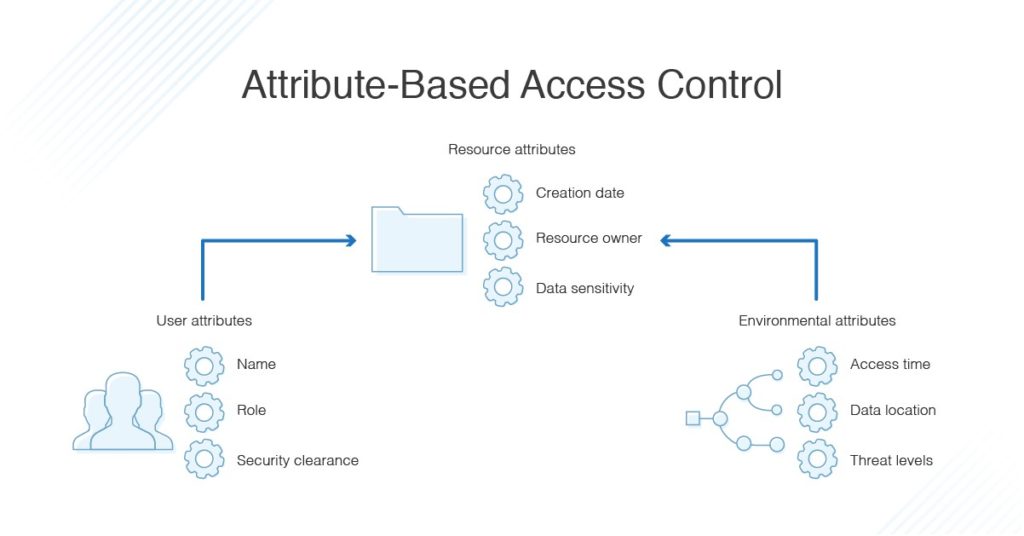
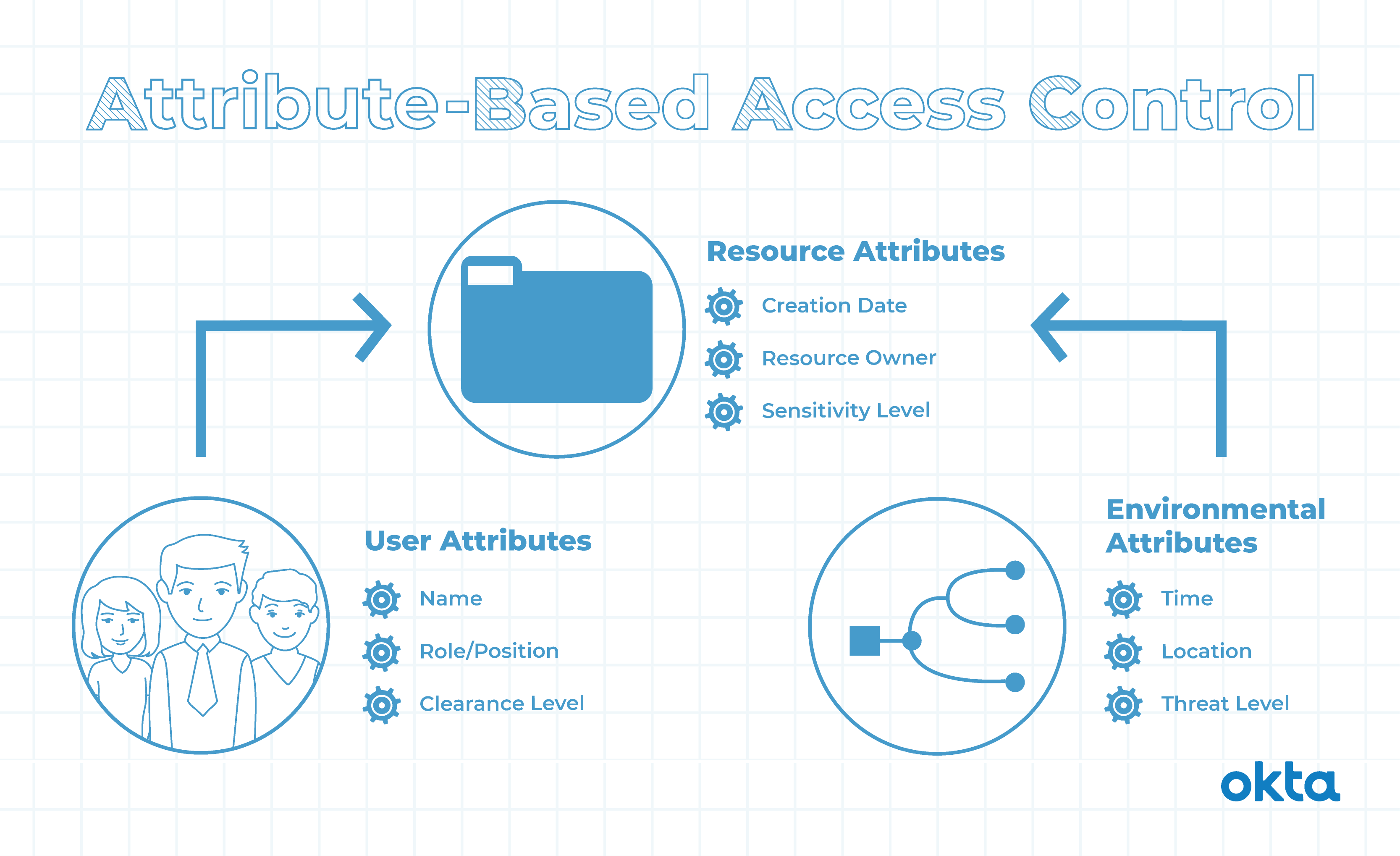
Limiting the visibility of sensitive data items through attribute-based access control (ABAC) - PegaWiki

Attribute Based Access Control (ABAC) in a microservices architecture for lists of resources - Stack Overflow
Attribute-Based Access Control in a Microservices Architecture | by Chetan Dravekar | Globant | Medium
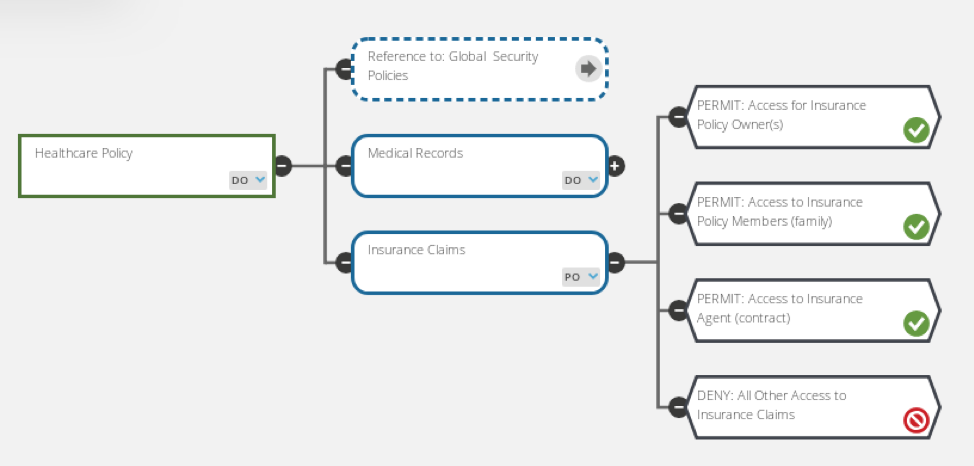
Why Attribute-Based Access Control Will Become the Standard Model for Large Enterprises - DZone Security

What are the advantages/disadvantages of attribute-based access control? - Information Security Stack Exchange

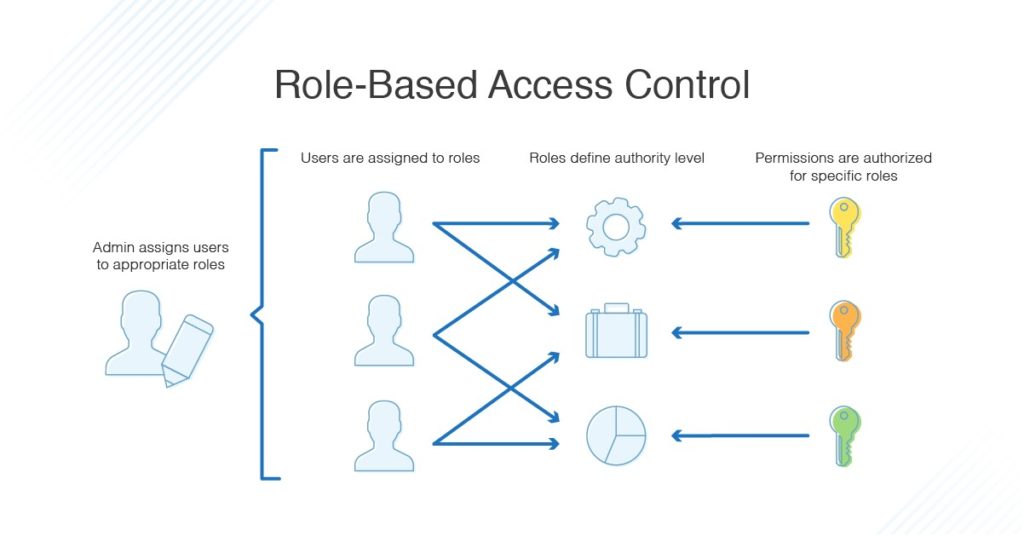
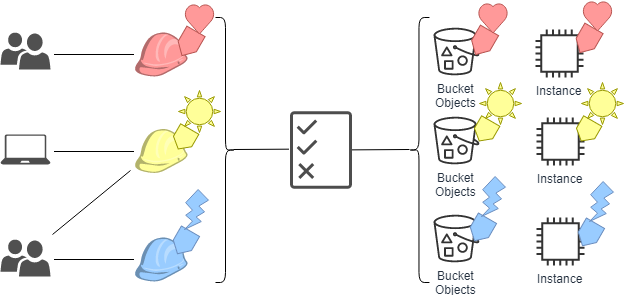

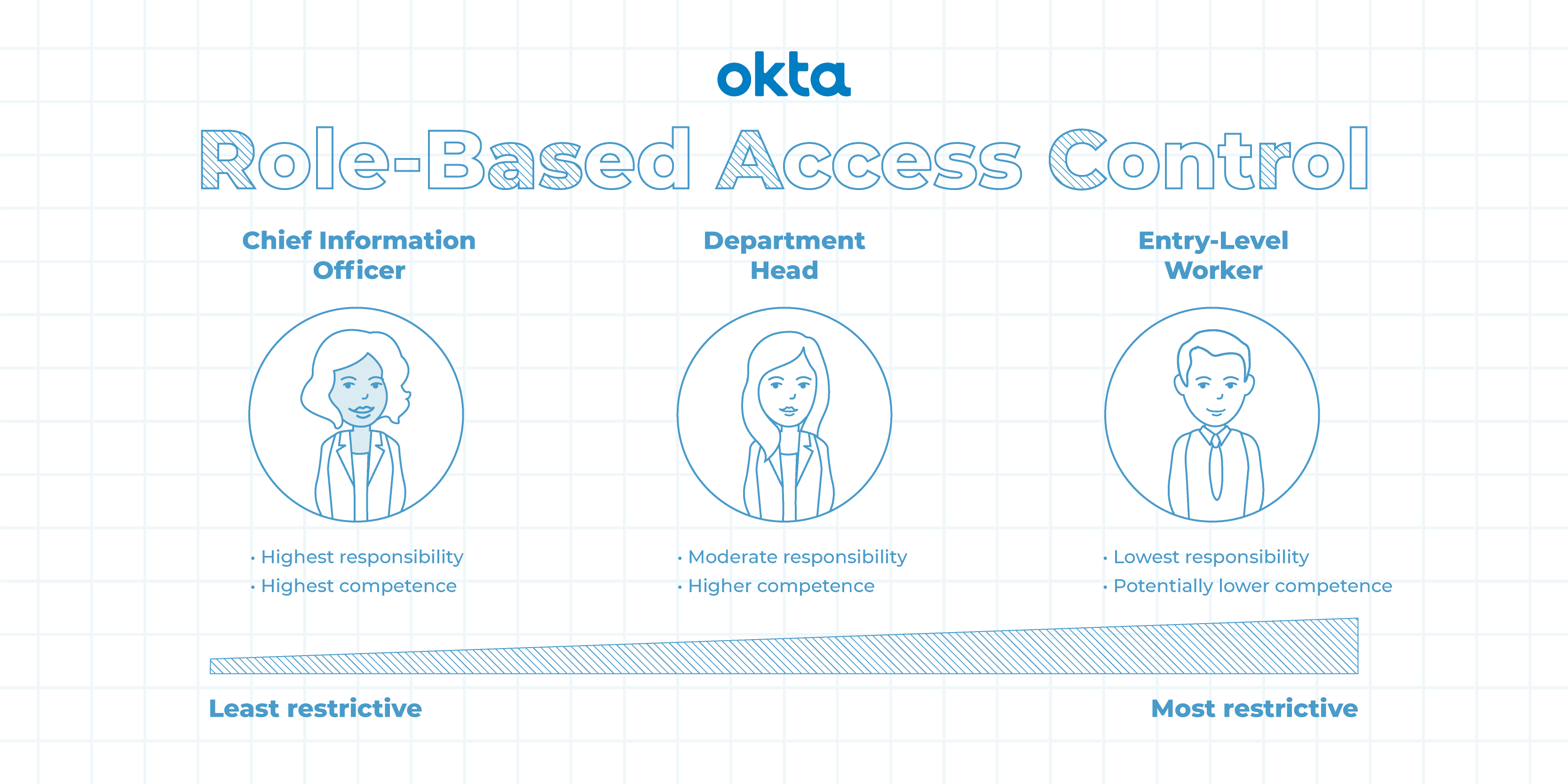





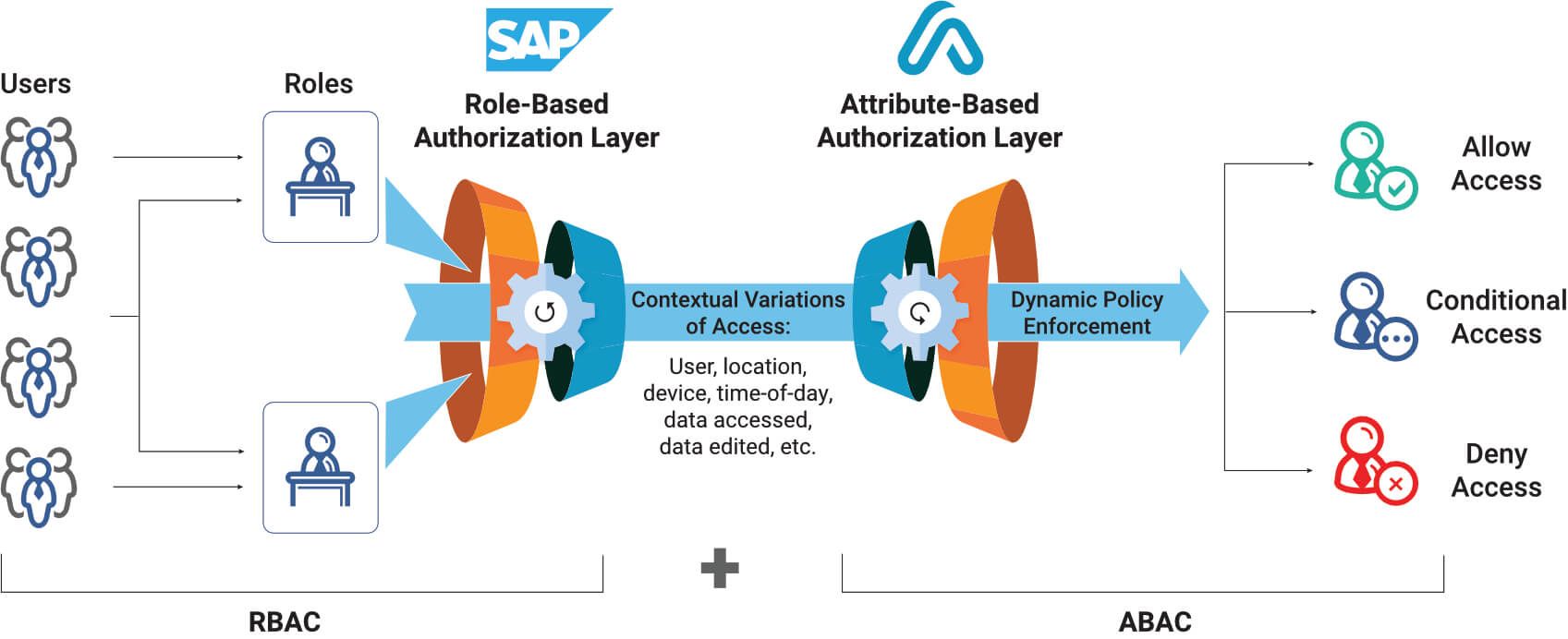

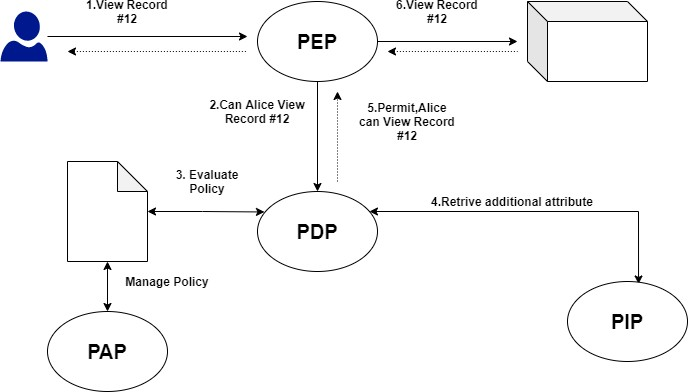
![PDF] Attribute-Based Access Control | Semantic Scholar PDF] Attribute-Based Access Control | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f2d698c5a1819b0cff0c8899b8a391c5721aa2b6/2-Figure1-1.png)