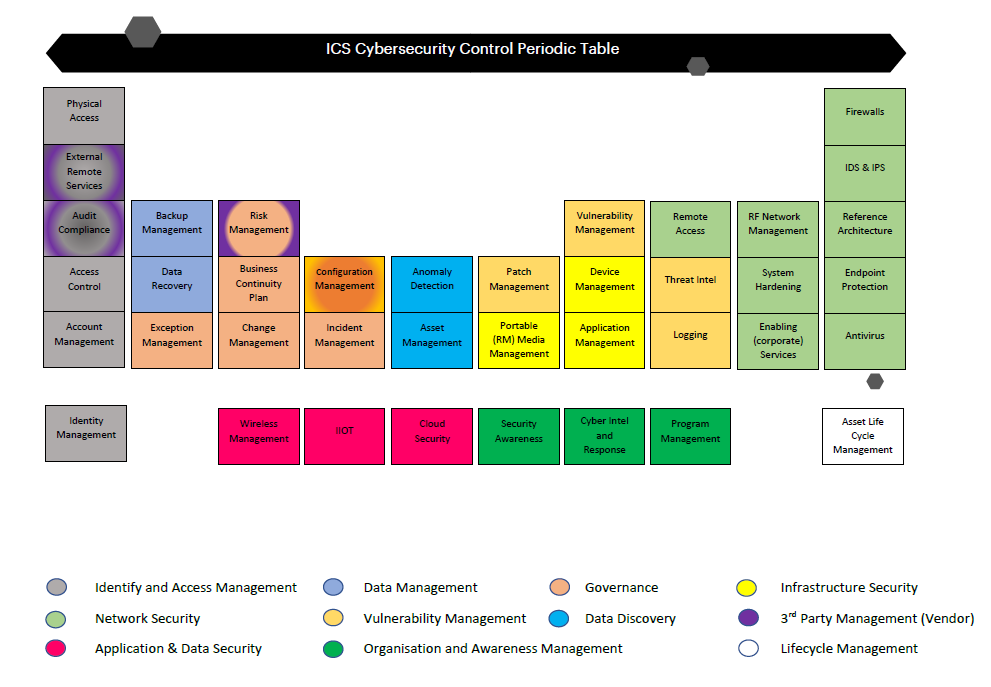
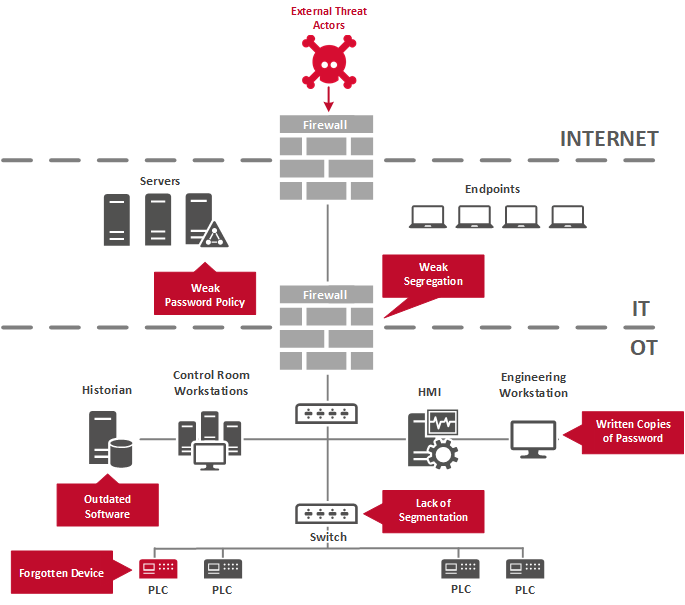
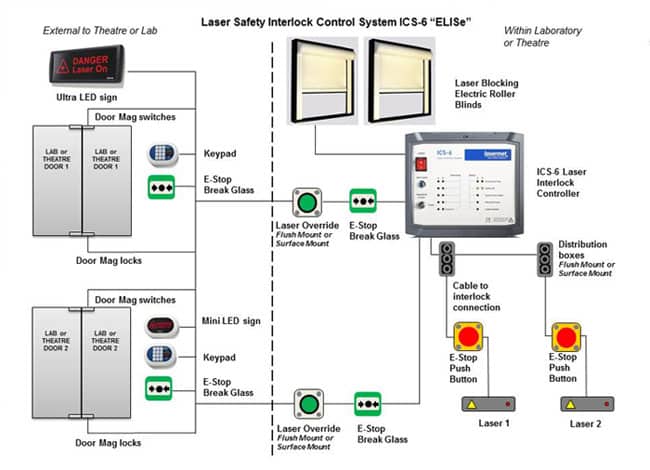
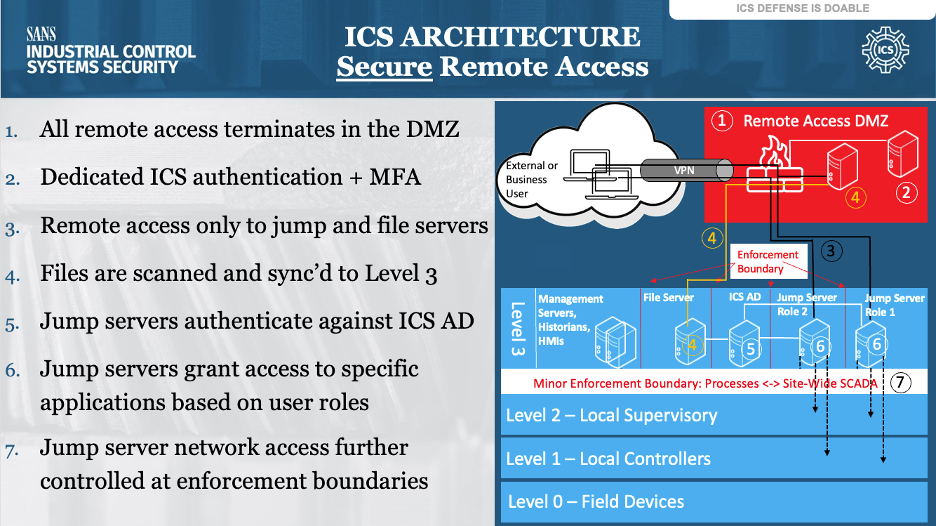
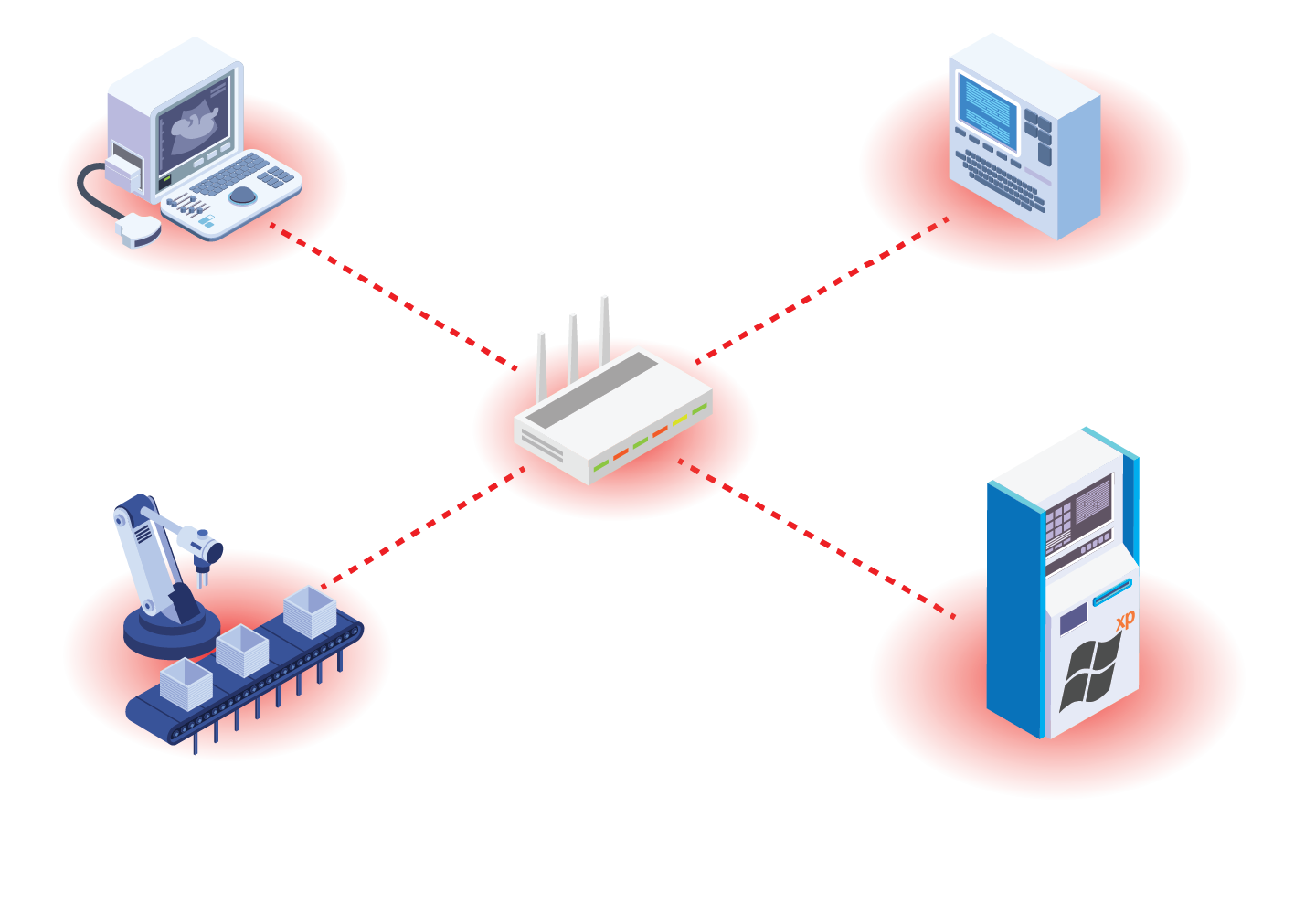
ICS Information Security Assurance Framework 18 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

ICS Companies Are Worried About Cybersecurity, But Are They Worried About Right Things?Security Affairs
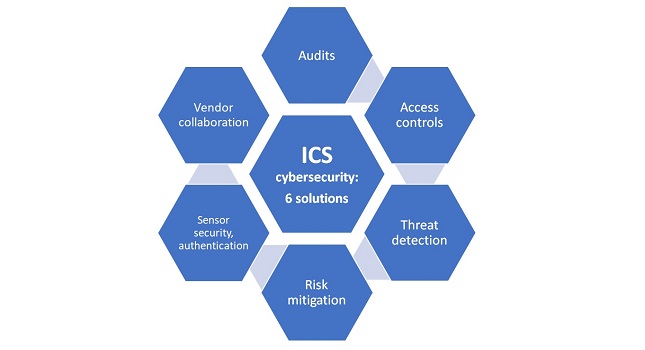
Six critical components of integrated cybersecurity for industrial control systems (ICS) | Control Engineering
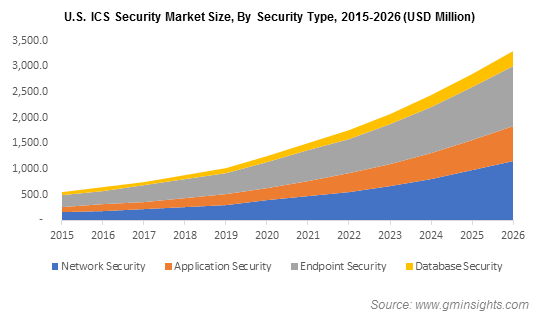


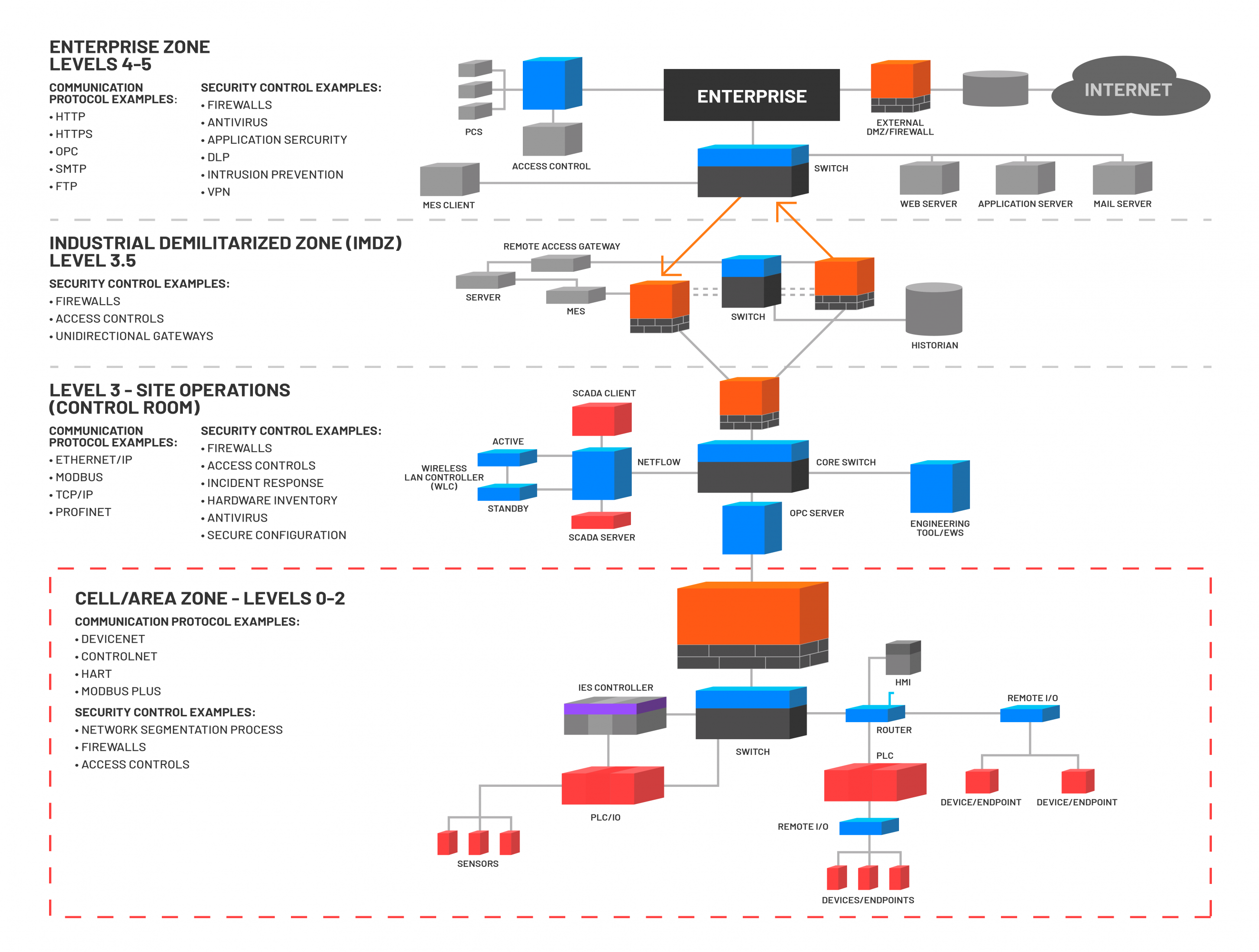
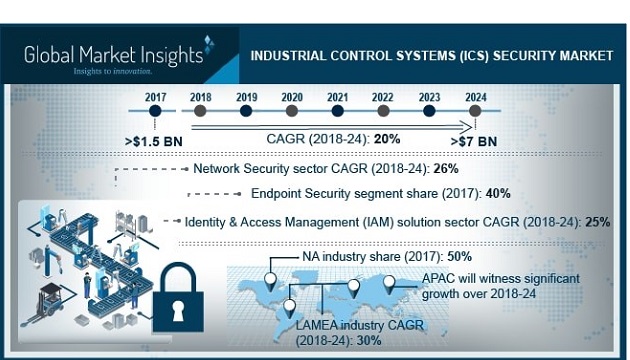

![ICS security methodologies [6] | Download Scientific Diagram ICS security methodologies [6] | Download Scientific Diagram](https://www.researchgate.net/profile/Ibrahim-Adeyanju/publication/344107065/figure/fig2/AS:932532904288257@1599344578293/ICS-security-methodologies-6.png)